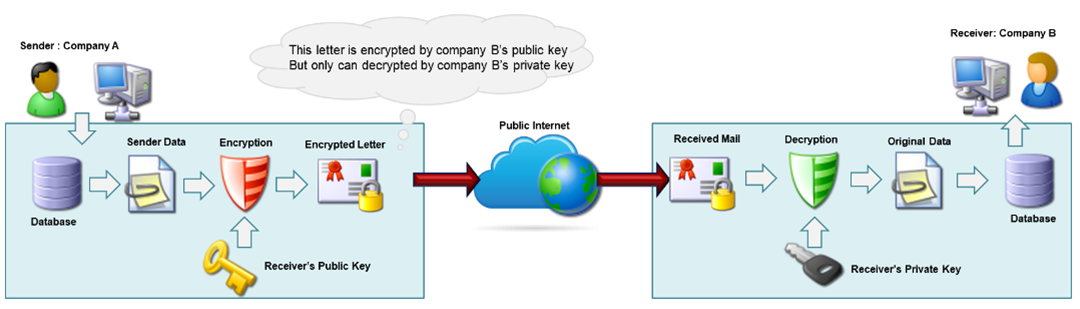
The following scenario illustrates how public key cryptography works.
Aaron from company “A” wants to send a message to Benita in company “B” via Internet but wants to ensure that if the message is intercepted no person other than Benita can read it. In this case, Aaron can use public key cryptography to encrypt his message.
Both Aaron and Benita would have a unique pair of public key and private keys. The private key should remain private on each side but the public key should be exchanged between the two parties. Aaron uses Benita’s public key to encrypt his message and sends it to Benita via a public network. Benita receives the message and uses her own private key to decrypt the information.

In order to verify that the message is really from Aaron (company A), the same technology can be used to provide a digital signature. Aaron uses his own private key to produce a digital signature and attaches it to the message. Benita will use Aaron's public key to verify this digital signature.
Thus, a secure communication between Aaron and Benita requires that both sides must know each other’s public key.
As explained above, each company running iTrak needs a unique pair of public and private keys. These keys are generated automatically by the system during first use of iGNet Plus. The private key is kept confidential in the system. However, to send or receive subject profiles to any other iTrak system the public keys must be exchanged between both sides.
To maintain a safe and secure key exchange between each pair of companies, iGNet Plus uses a “Contact Request” management system that uses a 16-digit temporary password to exchange public keys. iTrak users must establish a separate contact record for each pair of iGNet Plus communication.